 Search
Search


The subtle and often invisible nature of insider threats makes them particularly challenging to manage. Unlike external threats, insider threats are perpetrated by individuals within the organization, making them difficult to detect and prevent with traditional security measures. To effectively counter these threats, organizations must adopt a data-driven approach that not only identifies potential risks but also integrates cutting-edge technologies to streamline detection and response.
For effective insider threat management, the ability to comprehensively monitor and analyze various types of data is paramount. Each data type offers unique insights into employee behavior and potential security breaches, helping organizations detect patterns that may indicate malicious activity. A meticulous examination of data sources such as user activity logs, communication records, and financial transactions is essential for constructing a holistic view of potential risks. This integration of diverse data types not only aids in the early identification of insider threats but also enriches the contextual understanding of each incident, thereby enhancing the accuracy and effectiveness of any countermeasures employed. By prioritizing and scrutinizing certain critical data types (when accessible and permissible), organizations can proactively address vulnerabilities, safeguard their assets, and maintain operational integrity.
A robust insider threat management strategy begins with extensive data collection. Key data types include:
User activity logs — Provide insights into user behavior within networks, highlighting potential misuse or unauthorized access.
Email and communication records — Help detect unauthorized disclosures and suspicious communications, balancing security with privacy rights.
Network traffic data — Supply essential information for identifying unusual data flows that could signify attempts to exfiltrate data.
Physical access logs — Track access to secure areas, flagging unauthorized or suspicious entries.
Financial records — Can indicate changes in financial behavior that may suggest vulnerabilities or motives.
Psychological assessments and personnel files — Offer early warning signs of dissatisfaction or stress that could lead to insider actions.
Social media activity — Provides external context to an employee’s behavior and potential undisclosed associations.
By integrating these data types into a centralized platform, organizations can gain a comprehensive view of potential insider threats.
Once the necessary data is available, AI and generative AI (GenAI) technologies can play a crucial role in enhancing the capabilities of insider threat programs. These technologies enable rapid processing of vast amounts of data, identification of complex patterns, and generation of predictive insights.
Here are several ways AI and GenAI can be utilized:
Predictive analytics and scenario simulation — AI models can forecast potential insider actions, while GenAI can simulate various insider threat scenarios, allowing organizations to test and improve their defensive strategies.
Enhanced anomaly detection — AI algorithms can dynamically assess anomalies, with GenAI providing synthetic data that enhances the training of these models, leading to reduced false positives and improved detection.
Augmented decision-making — GenAI assists in decision-making by generating predictive insights and recommending prioritized actions based on potential impact.
Training and continuous improvement — GenAI can be used to create realistic training modules and continuously generate scenarios reflecting the evolving threat landscape, ensuring that defensive measures remain effective.
These and other AI and GenAI capacities are foundational to building an effective Risk Stratification Insider Threat Index and leveraging an Insider Threat Mitigation Framework.
The development of a Risk Stratification Insider Threat Index is essential to effectively identify, assess, and mitigate associated risks. This index provides a systematic approach to quantifying the potential dangers posed by insiders, enabling organizations to prioritize their response efforts based on the severity and likelihood of threats. By stratifying risk in this detailed and nuanced manner, organizations can allocate resources more efficiently, respond to threats more swiftly, and, ultimately, better protect their critical assets. This approach not only enhances security but also supports a culture of trust and safety within the organization, safeguarding its operations against the detrimental impacts of insider threats.
The process of managing insider threats via a Risk Stratification Insider Threat Index involves several key steps:
Data integration — Ensure all relevant data types are centrally analyzed while maintaining privacy and legal standards.
Baseline behavior modeling — Establish normal activity patterns to identify deviations.
Anomaly detection — Deploy statistical models or AI-driven algorithms to detect unusual behavior or risk indicators.
Threat scoring — Assign risk scores based on the severity and frequency of detected anomalies.
Contextual analysis — Incorporate external and personal contexts to refine the accuracy of risk scores.
Risk stratification — Categorize threats to prioritize responses effectively.
Monitoring and adjustment — Continuously refine models and strategies based on new data and insights.
Response protocol development — Establish clear procedures for different threat levels, from investigation to remediation.
This framework outlines a structured approach to mitigating insider threats by integrating advanced technologies such as AI, GenAI, and automation. It is designed to provide organizations with the necessary tools and strategies to detect, respond to, and prevent insider threats effectively, thereby protecting critical assets and maintaining organizational integrity.
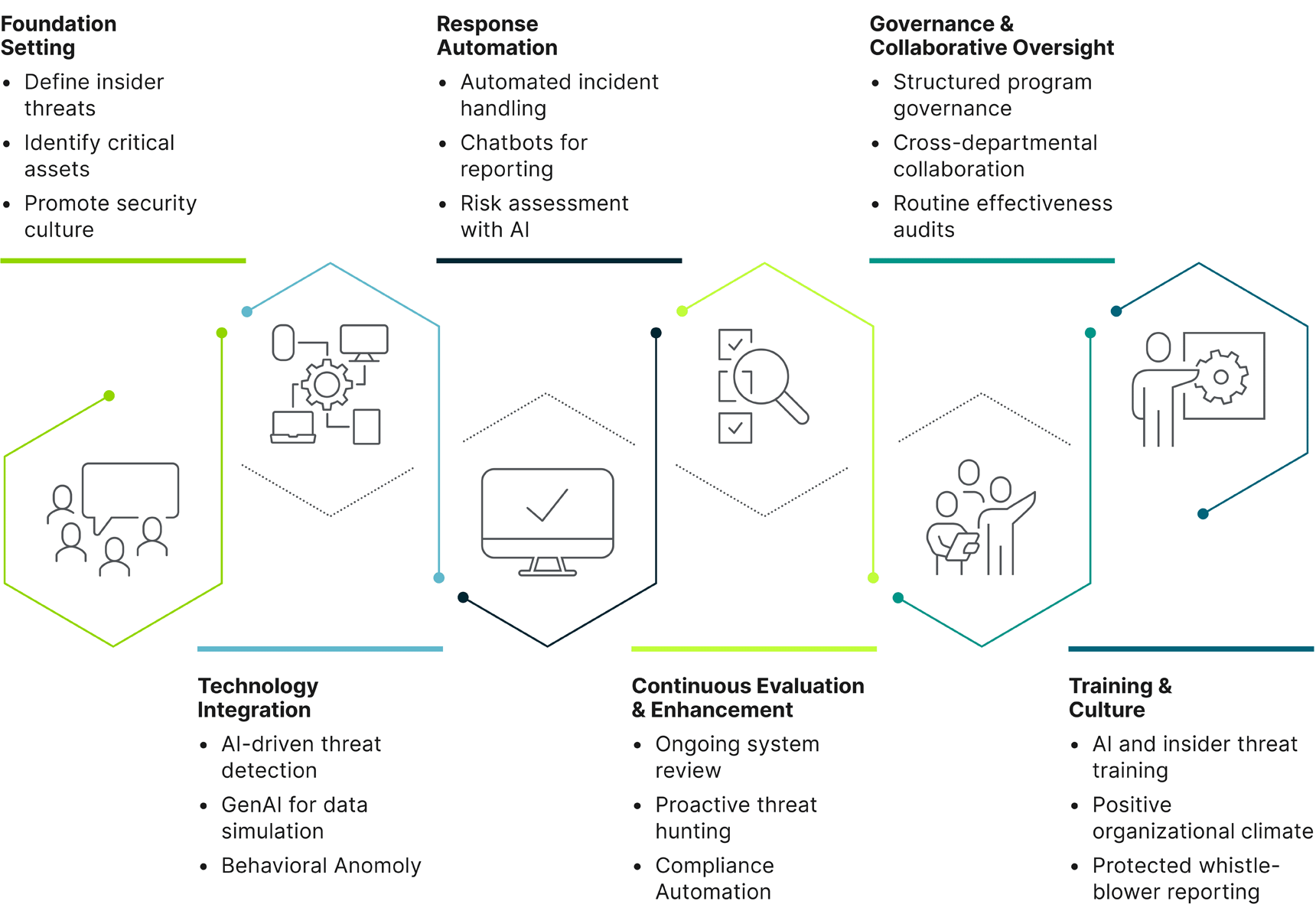
Our framework entails first establishing the three essential elements of a robust threat mitigation system, and then following through with three ongoing operational approaches:
Foundation setting
Technology integration
Response automation
Continuous evaluation and enhancement
Governance and collaborative oversight
Training and culture
The Risk Stratification Insider Threat Index and Insider Threat Mitigation Framework outlined in this white paper represent a holistic approach to safeguarding organizational assets against internal risks. By integrating advanced technologies such as AI, GenAI, and automation with a structured strategic framework, organizations can enhance their ability to detect, assess, and respond to insider threats more effectively and efficiently. This comprehensive strategy not only improves security protocols but also strengthens the overall resilience of the organization against internal disruptions.
Adopting this framework allows for a proactive security posture that dynamically adapts to new challenges and technologies. It promotes shrewd insider threat management that is not just about responding to incidents as they occur, but about preventing them through continuous improvement and innovation. Furthermore, the emphasis on creating a culture of security and collaboration across all departments fosters a more vigilant and responsive environment.
By committing to this approach, organizations can protect their critical operations from the potentially devastating impacts of insider threats. The framework provides a roadmap for creating a secure, vigilant, and adaptive organization that is well-equipped to face the complexities of today’s digital landscape and beyond. This is not just an investment in security but a cornerstone for sustainable operational integrity and trust within the organization.
Guidehouse is a global advisory, technology, and managed services firm delivering value to commercial businesses and federal, state, and local governments. Serving industries focused on communities, energy, infrastructure, healthcare, financial services, defense, and national security, Guidehouse positions clients for AI-led innovation, efficiency, and resilience.