 Search
Search


One of the most vital parts of building a successful supply chain risk management (SCRM) program is understanding the provenance behind the assets, data, software, and intellectual property in your supply chain. Supply chain provenance refers to understanding the origin or source, of goods and materials in a supply chain, and their “chain of custody.” Managing supply chain provenance risk is, therefore, critical for both public and private sector organizations. Commercial businesses that fail to address supply chain provenance risk can face negative impacts, such as financial loss, operational disruptions, reputational damage, and legal liability. For government agencies, the risks can have broader economic, national security, and societal impacts.
In an ever-changing and complex business environment, critical organizations are increasingly the targets of both hostile state actors and hackers. As the threat ecosystem grows more complex, understanding the supply chain risk landscape and the origins of an organization’s highly valued assets and their components becomes more challenging—and more important.
The global shift in the availability of goods; the possibility of counterfeit, reused, or substandard parts; cybersecurity and software vulnerabilities; and the need for alternative suppliers are formidable to navigate. Organizations often must now also uncover whether an entity in the supply chain has links to, for example, the Chinese Communist Party, China’s defense establishment, the predominantly Uyghur Xinjiang region in China, or has been involved with intellectual property theft or human rights abuses.
A systematic and risk-informed enterprise-wide program is essential to identify concerns and safeguard production, systems, data, sustainment, maintenance, security, platforms, suppliers, and products. The key is first understanding the risks and vulnerabilities throughout the supply chain, then setting a strategy for mitigating them. Building and operating a SCRM program is a crucial element in this vigilance.
Guidehouse’s experience and research show that US companies and agencies will likely continue to face major supply chain threats and challenges for the foreseeable future, including:
Cyberattacks focused on suppliers and vendor systems — A single breached supplier can compromise a network of its business partners.
Complex procurement, fragmented systems, and inconsistent company or business unit practices — These characteristics make it difficult to uncover provenance, chain of custody, and could result in noncompliance with laws and regulations.
Increasing use of counterfeit and/or substandard parts — Unknowingly incorporating faulty materials can compromise systems and adversely impact operations.
Natural or man-made disasters — Tornadoes, hurricanes, fires, floods, chemical spills, and other extreme events that disrupt supply chains can have knock-on effects and cascading impacts that adversely impact third parties.
Vendor risk — Limited transparency, understanding, and control over the entire vendor lifecycle process (including risk assessment, contracting, onboarding, hierarchy, monitoring, and offboarding) creates significant risk.
Activities such as mergers and joint ventures lead to new technologies and new vendors, and add to the difficulty of monitoring the supply chain. US legislation and strategy documents illustrate the high stake US companies and government agencies have in knowing who is in their supply chain from legal, reputational, operational, financial, and efficiency perspectives:
The National Defense Authorization Act for Fiscal Year 2022 — Requires the US Department of Defense to “develop capabilities to map supply chains and to assess risks to the supply chain for major end items by business sector, vendor, program, part, and other metrics.” ¹
The National Counter intelligence Strategy of the United States of America 2020-2022 — Identifies the protection of key US supply chains as one of the five pillars of the US strategy, intended to prevent attempts to compromise the integrity, trustworthiness, and authenticity of products and services purchased and integrated into the operations of the US government, the defense industrial base, and the private sector. ²
A strong SCRM program should incorporate the following areas: risk governance; risk appetite, tolerance, and culture; risk identification and assessment; risk response; risk reporting; and risk tools and technology. Integrating supply chain provenance into an SCRM program enhances and drives progress in the following areas:
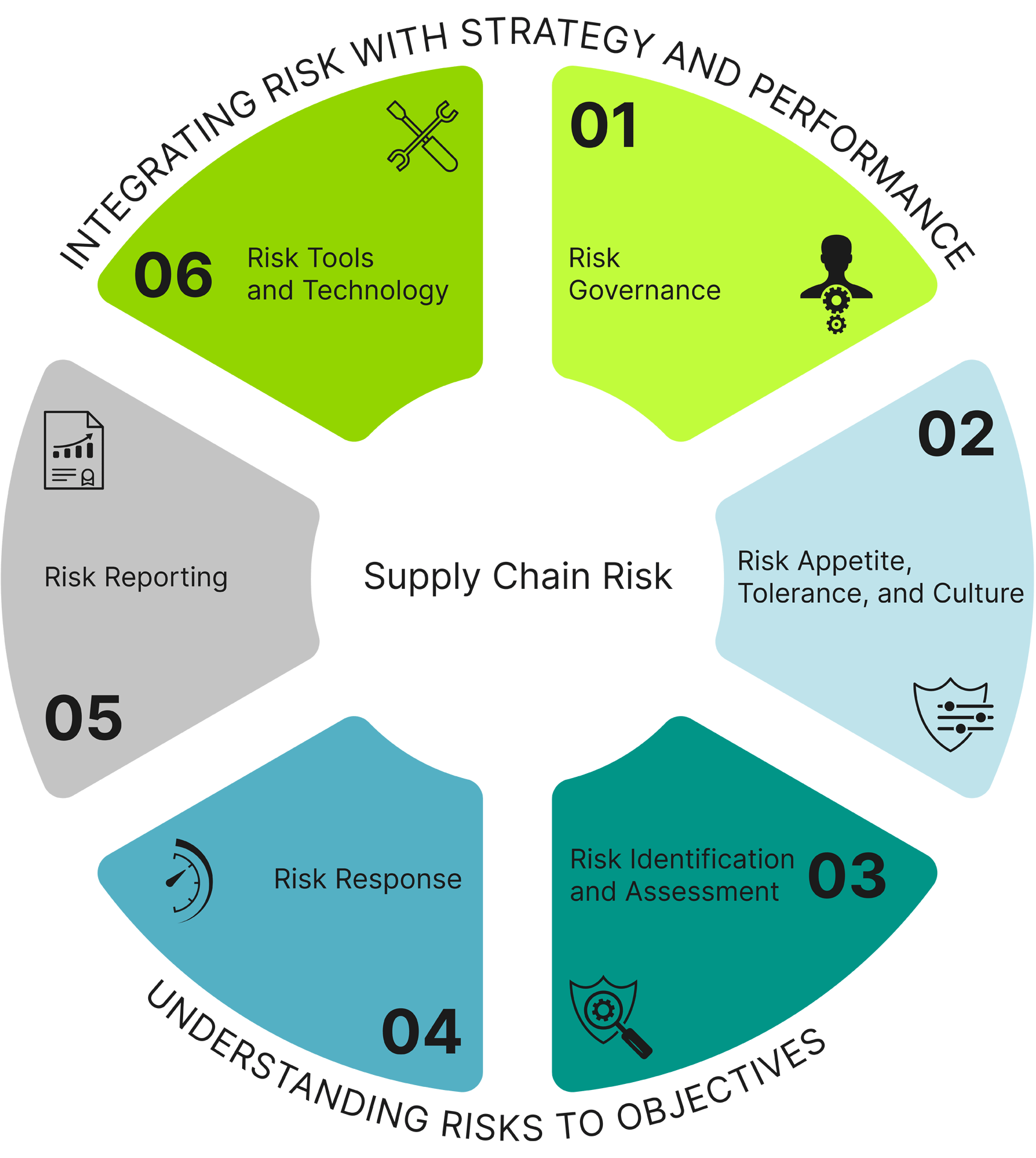
Risk Governance — The establishment of a system or body that determines and periodically reviews policies and determines how supply chain risk issues fit into the broader enterprise risk management of a company or government agency is key and establishes the guiding SCRM principles that run a supply chain-smart entity.
Risk Appetite, Tolerance, and Culture — In their operations, every business or government agency makes significant, routine decisions—implicitly or otherwise—about its risk appetite and tolerance and, therefore, its culture. For examples, in making selections and tradeoffs about the prices, service terms, past engagements, experience, reputation, financial wherewithal, and hundreds of other dynamics related to their suppliers, choices are being made about risk.
Risk Identification and Assessment — Identify high-value assets and their risk by conducting an illumination review of the assets’ supply chains, including suppliers and vendors, manufacturers, brokers, and freight forwarders.
Risk Response — Once provenance risks are identified and assessed, an organization’s risk management principles will drive decisions when possible. Risk management practices are compared to commercial and government prevailing practices to determine appropriate standard operating procedures and the most effective way to proceed for risk mitigation.
Risk Reporting — A provenance risk solution can be established as an ongoing, continuous monitoring process of reporting risks associated with the key supplier base as relevant changes occur.
Risk Tools and Technology — Especially in today’s world, there are all sorts of SCRM-related and other business tools and technology that can be used to help with SCRM in myriad ways, including determining the provenance of assets, data, software, and intellectual property that you’re considering acquiring or that is already in your supply chain.
The complexity of processes, vendor ecosystems, and assets creates numerous opportunities for things to go wrong, both “naturally” or as a result of threat actors. Without understanding supply chain provenance, organizations may lack insight into the chain of custody or location of origin, leaving risks in the supply chain inadequately identified, assessed, and prevented or mitigated.
Most SCRM-related efforts are narrow in focus and lack the depth to uncover security or operational risks that could negatively impact mission readiness and operational effectiveness. The complex dynamics of worldwide supply chains provide ample opportunity for everyday things to go off track, but also give bad actors the chance to make malevolent insertions into sensitive and important systems, data, and products.
This all takes place, furthermore, in a changing environment where software-based systems are more and more overtaking hardware-based systems, organizations are increasingly shifting to the cloud, and connectivity, shared services, crowdsourcing, and the use of machine learning are growing dramatically.
To protect and maintain smooth operations, organizations should especially—and certainly initially—focus on the provenance risks of critical and high-value assets. These assets may include essential data repositories; finished goods and products crucial to business, mission operations, or the revenue stream; industrial control systems; intellectual property; vital raw materials; security-related software; and key transportation or logistics assets.
Organizations that succeed in assessing and understanding provenance in these areas will improve the stability, reliability, and often cost savings of their supply chain and increase visibility into their risk exposure. Sometimes a critical supplier deep within a supply chain is actually supplying multiple Tier 1 suppliers.
Uncovering these situations can help organizations make more informed supplier decisions and avoid having a false sense of diversification. Supply chain provenance additionally helps organizations optimize spending on key vendors and raw materials, and decrease compliance risk through improved monitoring of supplier compliance obligations throughout the supply chain.
Guidehouse is a global advisory, technology, and managed services firm delivering value to commercial businesses and federal, state, and local governments. Serving industries focused on communities, energy, infrastructure, healthcare, financial services, defense, and national security, Guidehouse positions clients for AI-led innovation, efficiency, and resilience.